
A Primer on Vulnerability Management
Vulnerabilities are inescapable. Anyone who works in cybersecurity acknowledges that vulnerabilities are flaws in a system’s security that a malicious actor...
Find flaws in web, mobile, and IoT applications.
Expose risks in AWS, Azure, and GCP environments.
Ongoing testing to catch real-world vulnerabilities as they appear.
Live-fire exercises to sharpen detection and response.
Time-boxed security assessments across networks, apps, and infrastructure.
Simulated attacks to test detection and incident response.
Named security experts integrated seamlessly into your team.
Real-time detection and automated threat response.
24x7 monitoring and response by expert analysts.
Nonstop scanning to prioritize and reduce risk.
Ongoing scanning, triage, and compliance tracking.
Unified security platform powering all UV services.
Cross-platform toolkit for advanced red team ops.

Secure your code, infrastructure, and deployment pipelines before attackers exploit them.
Feb 3-5, 2026
Mar 19, 2026
Feb 19, 2026
UltraViolet Cyber is a practitioner-led MSSP delivering offensive and defensive security to Global 2000 and Federal clients. Built by former intelligence operators, we unify application security, red teaming, detection, and engineering under one roof. Our UV Lens platform replaces silos with integrated, outcome-driven operations.
UltraViolet Cyber
ZeroLogon is a Windows Netlogon vulnerability first detected in 2020. CVE-2020-1472 was assigned for this vulnerability. [5] While Microsoft has released appropriate patching for this vulnerability following its discovery with several updates since, it is important for companies to recognize that this vulnerability is still actively being searched for and exploited to gain unmitigated access to domain controllers and thereby entire networks. Please read on for more details on this vulnerability, its functionality and what steps can be taken to protect vital systems from threat actors employing this attack vector.
ZeroLogon leverages a weak cryptographic algorithm (AES-CFB8) that the Netlogon authentication process utilizes. Attack is done using 0 characters in Netlogon authentication parameters. Allows for password changes across all of AD, attacker gains access to disabling security features and allows for impersonation of any device in network/AD. [2]
Exploit Process:
Notably, ZeroLogon can be pulled into the Mimikatz toolkit, also. [1]
Impacket is used alongside ZeroLogon exploitation to pull hashes from the DC. Full domain takeover is possible utilizing this type of attack.
The ZeroLogon attack does need to come from a machine on the same LAN as the target and the spoofed login must function in the same fashion as a domain login attempt. Because AD must ‘see’ (recognize) the client attempting connection within the communication mechanism architecture (logical topology), external addresses would be extremely unlikely to have any success in exploiting this vulnerability. Hence, this vulnerability and exploitation thereof falls under the category of ‘Privilege Escalation’, for the most part. [2]
Microsoft revealed use of the ZeroLogon attack to access government systems with persistence attributed to Mercury APT group. [3] The Trickbot trojan has also been seen utilizing ZeroLogon to achieve objectives. [4]
In an article from the Healthcare IT Journal by Murphy Miller, some additional useful information pertaining to campaigns utilizing ZeroLogon and related activity preceding exploitation of the Netlogon vulnerability was presented, as follows:
CISA and the FBI revealed in the notification that attacks commence with the exploitation of legacy vulnerabilities located in VPNs and network access devices. In many attacks, preliminary access to networks was obtained via exploitation of vulnerability CVE-2018-13379 of the Fortinet FortiOS Secure Socket Layer (SSL) VPN as well as the MobileIron vulnerability CVE-2020-15505. Ransomware gangs are likewise taking advantage of the last-mentioned vulnerability subsequent to the advisory of a PoC exploit for the flaw.
Although the most current campaigns were performed exploiting the previously mentioned vulnerabilities, CISA/FBI advises that there are some other legacy vulnerabilities in Internet-facing infrastructure that may, in the same way, be taken advantage of in attacks for example:
Very recently, in an article published by ZeroFox, intel from threat actor Secdat9xx posted on the RAMP community site a sort of manual indicating that ZeroLogon is very much still being exploited ‘in the wild’ and essentially gave a how to guide in the manual:
ZeroLogon is a privilege-elevation vulnerability with a NIST severity score of 10.0 (critical). Successfully exploited, it enables threat actors to establish a vulnerable Netlogon secure channel connection to a domain controller using the Netlogon Remote Protocol (MS-NRPC). This can enable the attacker to gain domain administrator access. [6]
*Also including image shared by ZeroFox Intelligence showing the Secdat9xx post:
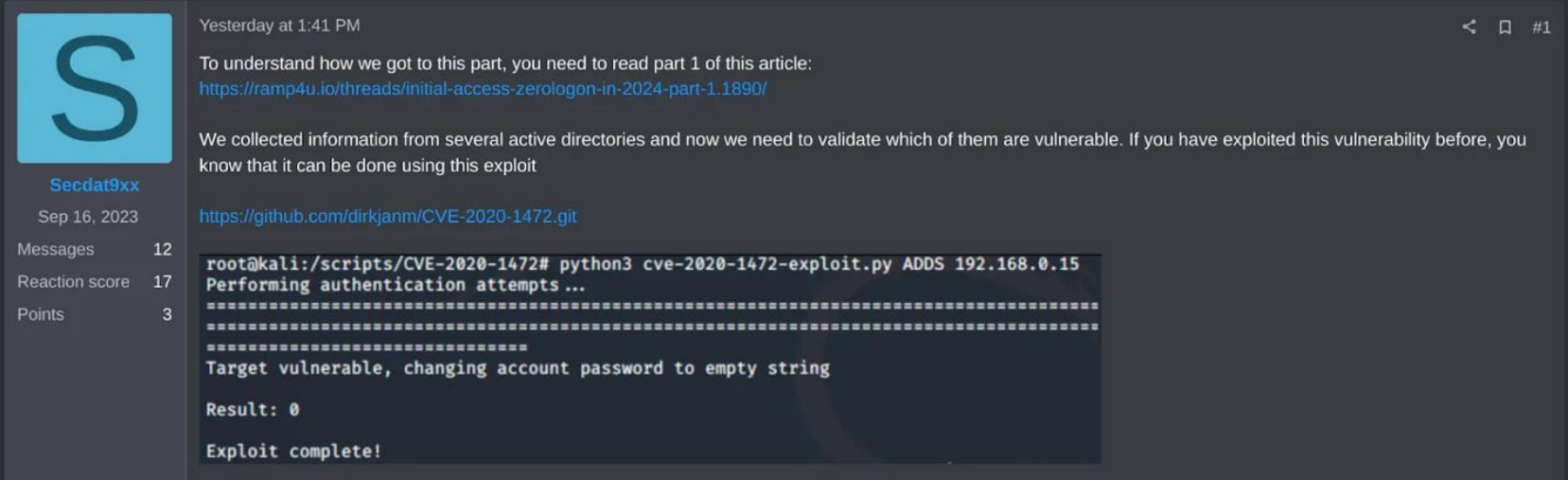
The ease at which threat actors can acquire the necessary tools to make use of and exploit this vulnerability is staggering; all that is required is the ZeroLogon PoC, CrackMapExec (both on GitHub publicly) and employ a Metasploit module to remove an administrator password. [6]
Microsoft suggests rejecting NetrServerAuthenticate3 requests with the first five bytes being identical as
well as rejecting unsigned/unsealed Netlogon channels on all Windows accounts. At this time, Microsoft should have further increased the scope of the patching that occurred to include rejection of insecure Netlogon sessions from non-Windows devices. MS fixed the vulnerability by enforcing RPC (remote procedure call) in Netlogon Protocol across all Windows devices. [1] [2]
[1] https://www.crowdstrike.com/blog/cve-2020-1472-zerologon-security-advisory/
[4] https://www.malwarebytes.com/
[5] https://nvd.nist.gov/vuln/detail/CVE-2020-1472
[6] https://www.zerofox.com/blog/the-underground-economist-volume-4-issue-6/
[7] https://woshub.com/zerologon-critical-active-directory-vulnerability/
We’re here to help. Get in touch for an initial conversation with one of our security experts and learn more about how UltraViolet Cyber can help you take cyber readiness and resilience to new levels.