UltraViolet Lens
The UltraViolet Lens Platform has an open architecture that enables us to ingest terabytes of Digital Exhaust from various telemetry devices each day. These can be anything from cloud platforms, security technologies, endpoint devices, IOT, OT, to our own platform generated content via our endpoint agents, vulnerability scanning, continuous automated red teaming, or cloud security posture assessments.
UltraViolet Lens Platform Features
- Outcome-based — Fully integrated platform delivered as-a-service
- No ingestion limits — More data equals more alerting fidelity
- Scalable Log Aggregation — Seamless Log Ingest/SIEM integration
- Detections-as-Code — Continuous search using vast detection library and escalate all mapped to MITRE ATT&CK framework
- Threat Intelligence — Included Indicator Database with Maturity Model
- Response Actions — 3rd party integrations via API allow for response actions at machine speed based on automated playbooks
- Modernized Dashboarding and Reporting — Integration ServiceNow
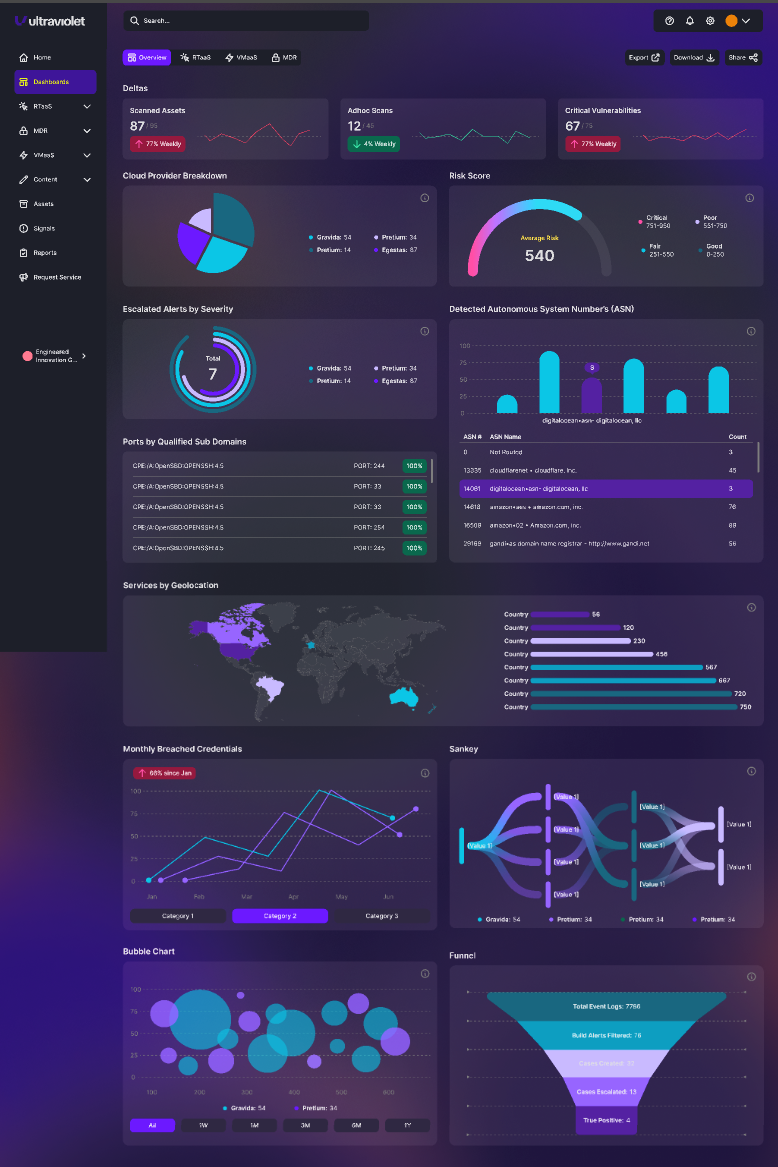
Platform Deliverables
Visibility
Observability Platform
Threat Hunting
Threat Intelligence
Detection as Code
SOAR
Analyst Investigation and Response
Generative AI / ML
Modern Agent
Customer Portal
Ticket System Integration
Your Experts, Amplified.
We deploy our SOC-as-Code attacks and detections as close to the workload as possible to help attain signal through the noise of all that Digital Exhaust.
Leveraging the power of BIG DATA, we also apply our SOC-as-Code attacks and detections to the entirety of that Digital Exhaust. Every minute we run thousands of unique "as-code" queries to find signal in the noise.
This unique feature gives us the power to time travel. When a new attack pattern becomes known (either publicly or we've discovered a new attack path via our RTaaS service) we are able to run it against previous digital exhaust to see if you've been compromised or have had additional exposure.
To put a finer point on it, we run all our SOC-as-code against newly created digital exhaust (detect and attack in the present) as well as against legacy digital exhaust (detect and attack in the past). Once we've separated the Signals from the noise our experts validate and collaborate with you to provide actionable validated secure outcomes to you. Those outcomes help you focus on what is required to be done right now, today to help improve your posture and defend like the adversary.