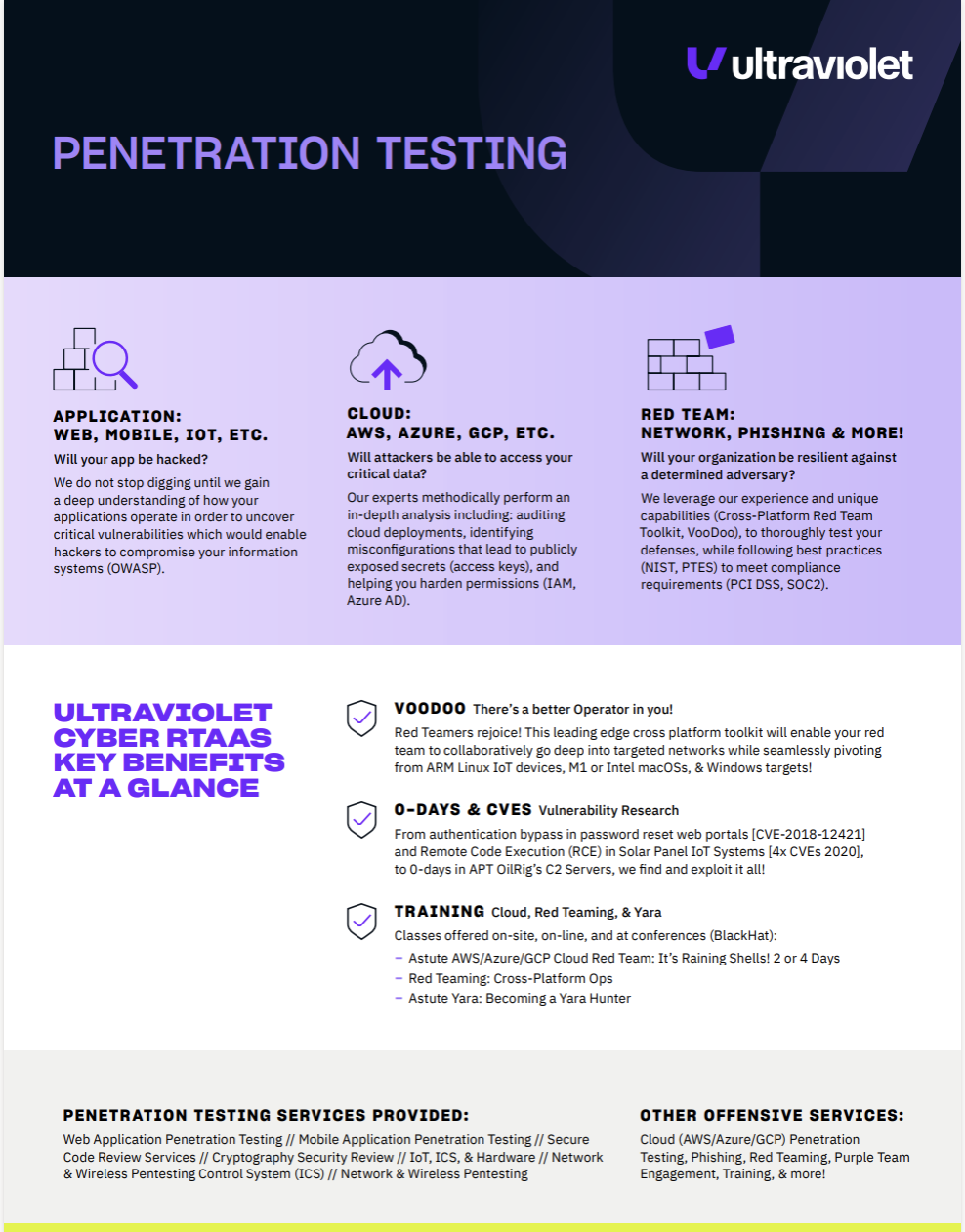
Penetration Testing as-a-Service
Advanced threats are relentless—your penetration testing needs to be, too
Does your adversary limit their attacks to once a year? Of course not, which is why you should be relentlessly testing your attack surface to stay ahead of threats. Leverage automation and a bounty of microservices to better identify and mitigate security risks. Now you don’t have to choose between attack surface management, vulnerability scanners, or any other point solution. UltraViolet Cyber provides unified security solutions, delivered.
HUMAN EXPERTISE— AMPLIFIED BY AUTOMATION
Continuous threat exposure management (CTEM) combines human expertise with enhanced automation to continuously test and assess various environments. A multitude of touch points demands a comprehensive solution. Why choose?

A cloud-native platform driven by automation
Pen testing is an essential part of an offensive security strategy. Continuously attack against a system, network, or application to identify and measure risk.
Stay ahead of would-be attacks
Attack surfaces change and evolve. Threat actors target these borderless environments, searching for vulnerabilities. Pen testing ensures you know where weaknesses are before the attacker does.
Identify & protect
Constant real-world threat actors demand constant vigilance and defense. Think of pen testing as a team monitoring your castle 24/7, searching for weaknesses, assigning jobs to be done. With a world-class ability to identify and protect against risk, you gain the confidence to focus on business goals, knowing your castle is secure.
FOCUS ON KEY BUSINESS OBJECTIVES
The only way to detect and respond to today’s most advanced threats is to leverage machine power that augments human intelligence & intuition.
Expert support
Eliminate the need to frantically search for more responders—our team bolsters your team and conserves resources so you can focus on strategic goals.
World-class training
Level up with UltraViolet Cyber’s Cohort program, which provides critical security knowhow for your existing IT staff, all at a fraction of the cost of hiring more staff.
Investment consolidation
Maximize your existing security investments and consolidate spend across SIEM, SOC, & Offensive Security.
Stay evergreen
Continuously adding new capabilities to the UltraViolet Cyber platform gives customers an arsenal of top-tier solutions to keep up with the fast-moving security industry.
No surprises
Fixed cost or predictable user-based modeling gives you the power to accurately forecast your budget.
Red team + blue team = UltraViolet
UltraViolet Cyber validates every blue team defensive escalation with a red team whose pedigree is from the US intelligence community, deploying relentless threat hunters armed with rich security analytics to respond to operation-critical incidents.

Human led; technology enabled
Uncover vulnerabilities and exploit them in targeted information systems, networks, IoT, cloud (AWS, GCP, Azure, etc.) and/or applications (web, mobile, etc.) within a set time domain to provide the highest ROI.
Real-time access with Red Team
Your adversary doesn’t work on a defined scope and timeline. We continually mimic advanced attacks and test your defenses using adversary simulation to discover unique attack vectors and then apply offensive TTPs.

On-demand reporting
The rise of mobility, cloud, micro-services, containerization & SaaS means defining your attack surface is difficult. We make it easier with centralized reporting. Delivered when you want it, from our Red Team to your customer portal.
IRON SHARPENS IRON
UltraViolet Cyber’s industry experts and former NSA operators know the enemy. Using a comprehensive set of relentless assessment capabilities across your entire attack surface, we’ll enforce offensive security techniques, so you truly understand imminent risk.
Renowned experts—applying offensive defense just for you.
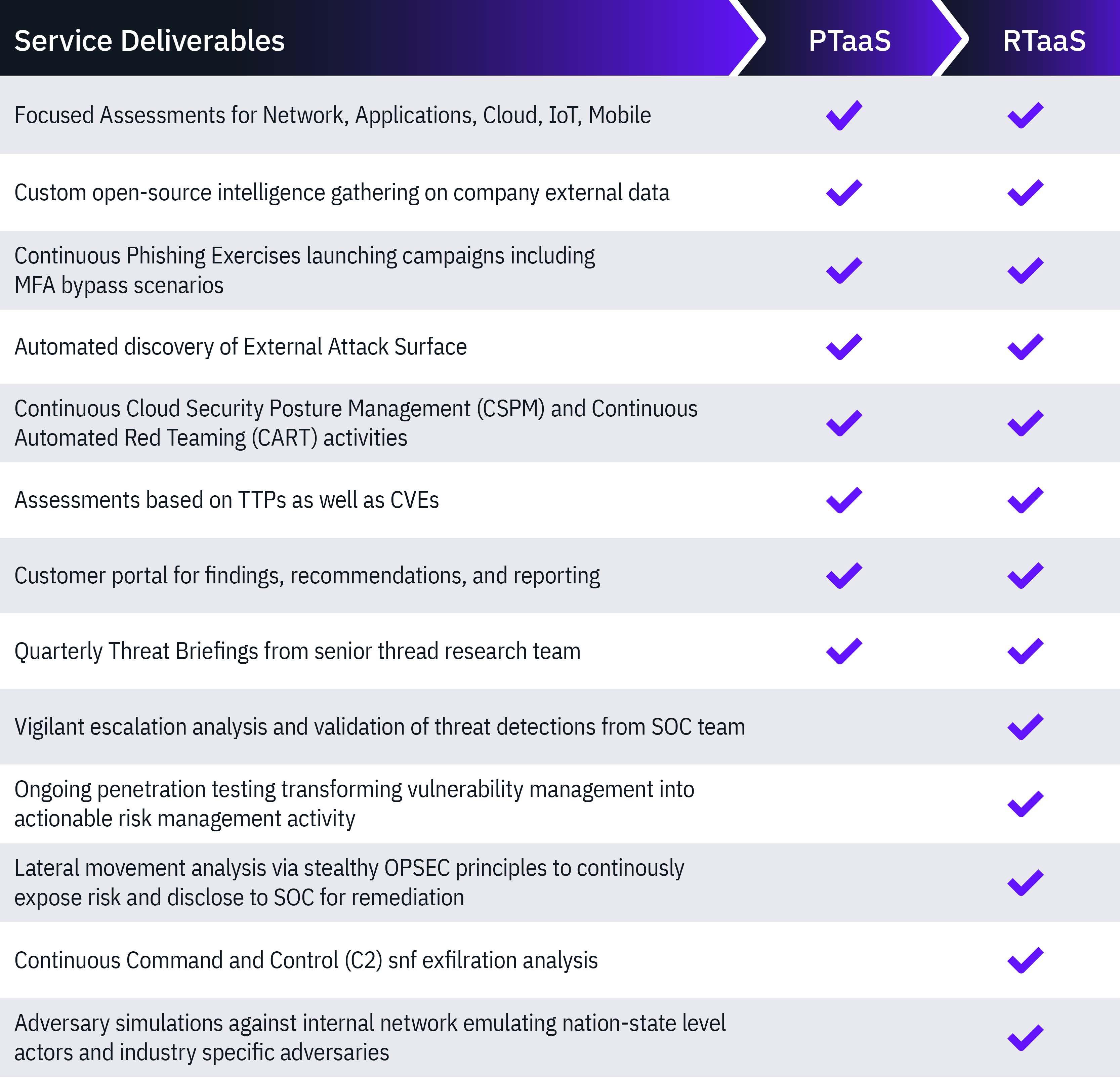
Attack scenarios that focus on the real-world risks
Leverage a range of TTPs to craft customized attack scenarios designed to replicate the modus operandi of real-world attackers.
BOOST EFFICIENCY & UPGRADE SECURITY
Security teams need unity and streamlined processes to protect customers against today’s most pressing cyber threats. There are few things more important in the digital age than keeping would-be attackers out of private environments containing sensitive data. Simply put, red and blue teams, with their attendant expertise and skills, are stronger together. That strength translates not only to the customers they protect, but to their own organizations. A unified security solution lets organizations respond to threats faster, stay agile, and reduce costs.
Empower security with automation
Streamline processes, collaborate better, eliminate discord, and improve security
Human led; tech enabled
Offensive security ensures you prepare, execute, and prosper today—and in the future.

See how UltraViolet Cyber Pen Testing increases your security effectiveness & efficiency.
READY TO SEE HOW ULTRAVIOLET CYBER'S PEN TESTING AS-A-SERVICE WORKS?
Take control of your imminent cyber risk with continuous real-world threat emulation across your complete attack surface to discover and eliminate risks.
 High-Scale SIEM Migration across 70TB/day and 4,000 detections
High-Scale SIEM Migration across 70TB/day and 4,000 detections

 OT\ICS: Hidden Equipment with Quiet Risks
OT\ICS: Hidden Equipment with Quiet Risks UltraViolet Cyber Acquires Black Duck’s Application Security Testing Services Business
UltraViolet Cyber Acquires Black Duck’s Application Security Testing Services Business UltraViolet Cyber Named to Inc. 5000 List of America’s Fastest-Growing Private Companies in 2025
UltraViolet Cyber Named to Inc. 5000 List of America’s Fastest-Growing Private Companies in 2025